Logicmojo - Updated Jan 11, 2024
Logicmojo - Updated Jan 11, 2024
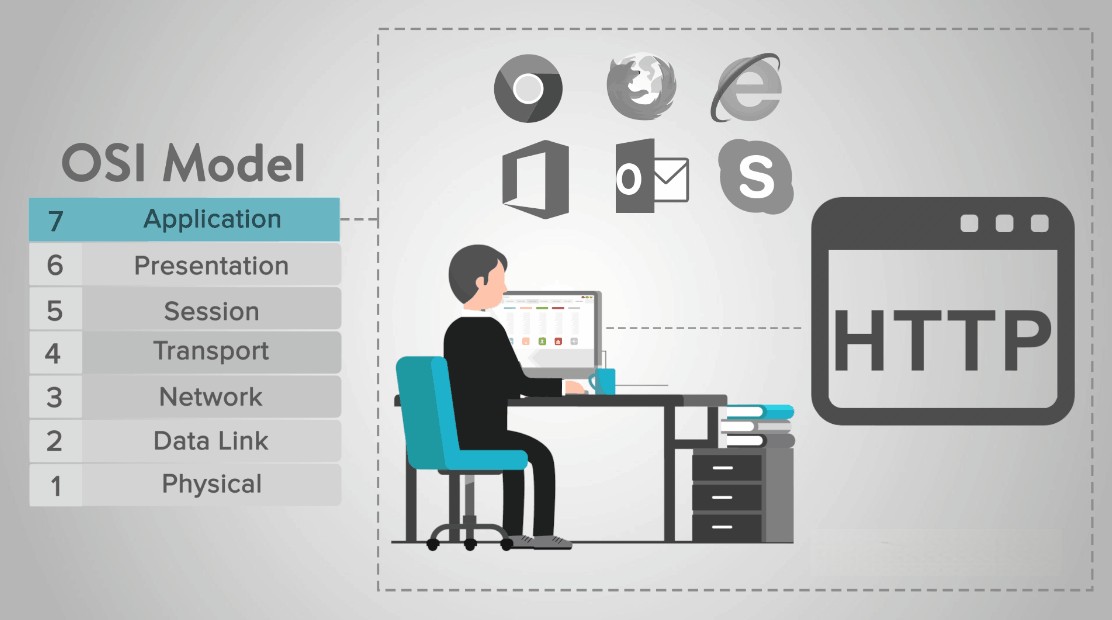
A theoretical framework for explaining the operations of a networking system is the Open Systems Interconnection Model (OSI Model). The OSI model categorises computing functions into a global set of rules and standards to enable interoperability between various devices and applications. The OSI reference model divides the interactions between computing systems into seven abstraction levels: physical, data link, network, transport, session, presentation, and application.
When network computing was still in its infancy, the International Organization for Standardization issued The OSI in 1984. (ISO). Even though it doesn't always correspond directly to actual systems, the OSI Model is nevertheless used to describe network design today.
Why the OSI model?
So, what's the deal with this conceptual model? Why use it when we can just talk about each networking system's infrastructure?
Because networks are inherently complicated. Layers are used in the model to provide a high-level explanation of what is going on within a networking system. It defines what happens in a communication system without getting into the nitty-gritty of the technology that underpins it. The OSI model's framework makes it easier for people to explain difficulties in a networking system and the relationships between the system's components.
When a network fails, for example, the OSI gives a mechanism to immediately pinpoint the problem: Is it an application problem or a hardware issue?
The Internet (or any network) is a complex system made up of a large number of hosts, routers, data lines, applications, protocols, hardware, and software. We need a mechanism to understand everything at a high level, otherwise we'll become quite confused! And it is here that the OSI model comes into play.
A communication system is divided into seven abstraction layers by the OSI. The layers are as follows:
Application layer
Presentation layer
Session layer
Transport layer
Network layer
Data Link layer
Physical layer.
Characteristics of OSI Model
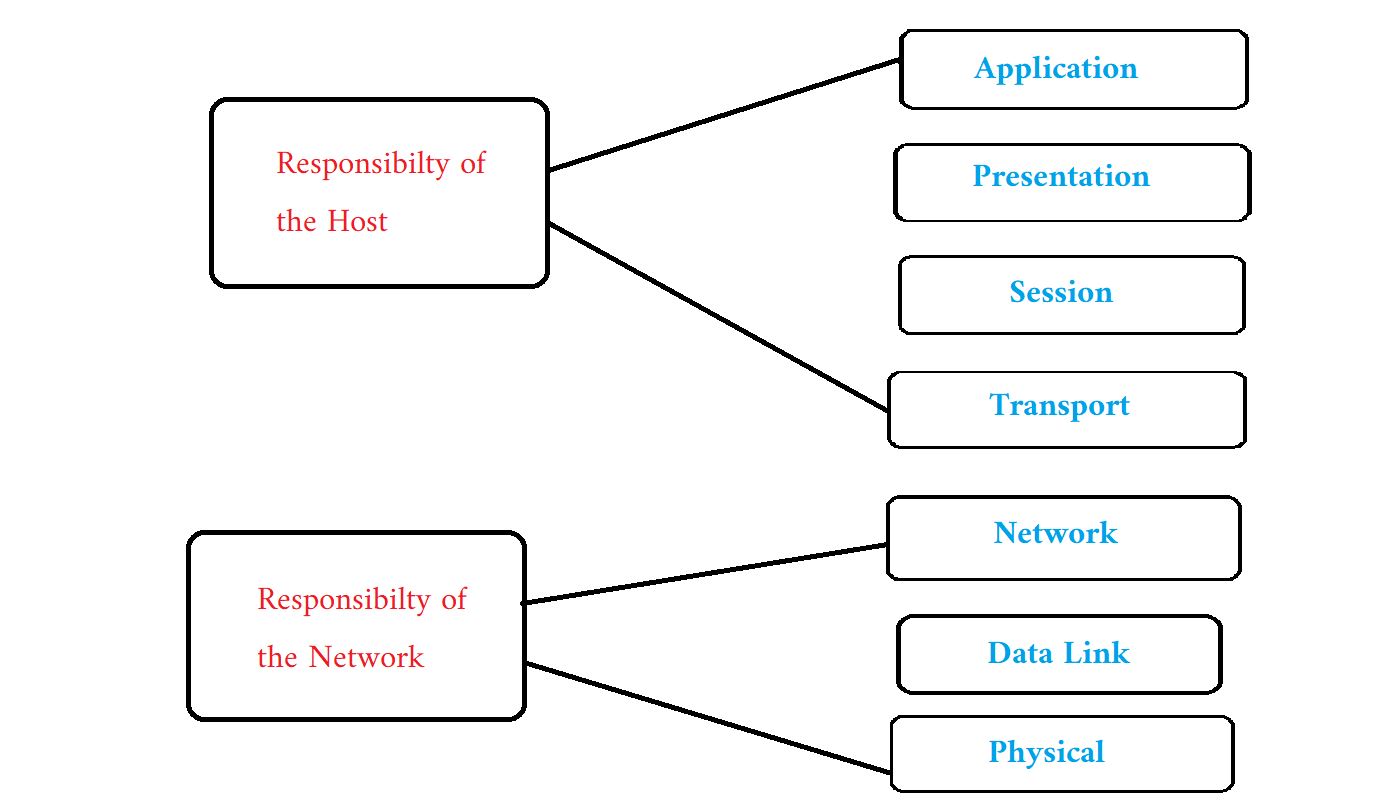
The OSI model is separated into two groups. The Host is responsible for one group, while the Network is responsible for the other.
The layers that the Host is in charge of are as follows:
Application Layer
Presentation Layer
Session layer
Transport Layer
And the levels that fall within the Network's control are –
Network Layer
Data Link Layer
Physical Layer
The hosts' responsibilities include encryption, session management, segmentation, flow control, and so on. The network's tasks include path to router packet, congestion control, network identification, and so on.
The layers
Starting with the application layer, let's break down the OSI model from top to bottom.
Application Layer
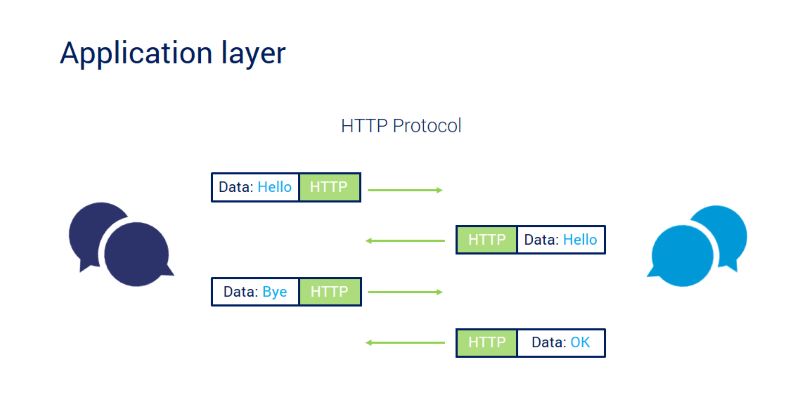
The only layer with direct access to user data is this one. The application layer is used by web browsers and email clients, for example, to establish communications. The application layer, on the other hand, is responsible for the protocols and data manipulation that the software employs to present relevant data to the user. Application layer protocols include HTTP and SMTP (Simple Mail Transfer Protocol is one of the protocols that enables email communications).
Presentation layer
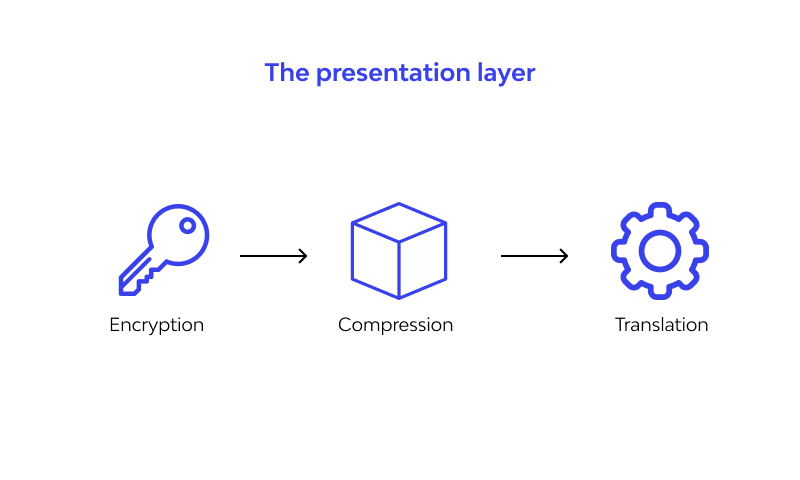
The presentation layer is also known as the "translation layer." Between the application layer and the data layer, it "translates" data. Because data from and to the application layer isn't always in the format required for network transmission, it must be translated and "presented suitably" to the next layer. Layer 6 is responsible for preparing data for use by the application layer; in other words, layer 6 makes data accessible to applications. The presentation layer is in charge of data translation, encryption, and compression.
Layer 6 is responsible for applying encryption on the sender's end and decoding encryption on the receiver's end in order to provide unencrypted, readable data to the application layer if the devices are communicating via an encrypted connection.
Finally, the presentation layer is responsible for compressing data received from the application layer before passing it to layer 5. This improves transmission speed and efficiency by lowering the quantity of data transferred.
Session layer
The session layer is in charge of maintaining "sessions" between machines. In order to provide authentication and security, a "session" must be created for two devices on the network to connect. This layer is responsible for establishing, managing, and ending these sessions. The purpose of this layer is to establish and maintain communication between the two devices. The session is the span of time between the start of a communication and the finish of it. The session layer ensures that the session is kept open for as long as it is needed to send all of the data being exchanged, and then closes it quickly to avoid wasting resources.
Network Basic Input Output System (NetBIOS) and Remote Procedure Call Protocol (RPC), among others, are examples of Session layer(Layer 5) protocols.
Transport layer
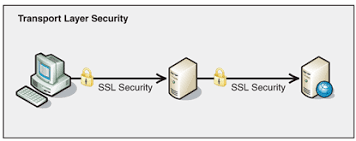
The transport layer is the network's "traffic control." TCP (Transmission Control Protocol) and UDP are two examples of protocols in this tier. The transport layer also handles flow control and error control. Flow control determines the appropriate transmission speed to avoid a sender with a fast connection overloading a receiver with a slow connection. On the receiving end, the transport layer performs error control by verifying that the data received is complete and, if it isn't, requesting a retransmission.
What is flow control?
Flow and error control are other critical aspects of assuring a network's correct operation. Network congestion can occur when too much data is delivered at once. The transport layer protocols must then decide which data to send first and in what sequence to send it in order to achieve the greatest overall efficiency. Even yet, data packets can occasionally arrive damaged or out of sequence. This layer's job also includes figuring out how to get the original data back if that happens.
Network layer
The network layer serves as the network's "post office." It is in charge of data routing from the source to the destination. The Internet Protocol (IP) and several routing protocols are important protocols on this tier. On every complex network, data must be sent from point A to point B in order to go from point A to point B. But where is the B-spot? What path does the data take to get there? The network layer is in charge of all of these responsibilities.
For example, where is the server that stores logicmojo.com homepage? What part of the network is it on? The IP protocol identifies devices on a network in a unique way, allowing each transmission's destination to be determined.
Data link layer
In the same way that the network layer allows data to be transmitted between two devices on the same network, the data connection layer allows data to be sent between two devices on the same network. Packets from the network layer are decomposed into smaller units known as frames by the data link layer. In intra-network communication, the data link layer, like the network layer, is responsible for flow control and error control (The transport layer only does flow control and error control for inter-network communications).
Physical layer
Finally, there's the physical layer. The physical layer is the lowest layer of the OSI model, and it refers to the part of the network that is in charge of the actual "on-the-wire" transfer of information. This layer is referred to as the "hardware layer." The choice of cable type, network structure, and radio frequencies are all implementation questions in this layer.
Advantages Of OSI Model
⮞ It establishes a common platform for software developers and hardware manufacturers to collaborate on the development of networking solutions that can connect with one another over the internet.
⮞ It aids network administrators by breaking down huge data transfer processes into smaller chunks.
⮞ It avoids changes in one layer from impacting other layers due to layer independence.
⮞ Multiple-vendor development is possible thanks to the standardisation of network components.
⮞ It decreases complexity while speeding up evolution.
Why do we still use the OSI Model?
Practitioners must keep a number of factors in mind when it comes to security. The OSI (Open Systems Interconnection) design provides the principles needed to handle both technical concerns and dangers inside a networking stack.
Despite the fact that information security is shifting to a cloud-first architecture, the OSI model is still essential. The following are some of the reasons why the OSI Model is still useful:-
⮞ Aids in the detection of threats across our entire tech stack
⮞ Allows for a data-centric security posture to be adopted
⮞ Allows for cloud adoption by prioritising security
⮞ It also protects cloud infrastructure
Important Terms
Mac address: The 48-bit or 6-byte long MAC Address (Media Access Control) contains the Hexadecimal code. It is the address that is assigned to each network device individually. Because it comprises the address of the physical network device from which data will be delivered, MAC address is also known as physical address.
Ip address: It is the address that has been uniquely determined by the network system. It is a 32-bit or 4-byte address (in IPv4), with each byte having an address range of 0-255.
HTTP (Hypertext Transfer Protocol): is a protocol that allows a browser to send web pages, pictures, and text across the internet.
HTTPS (Hypertext Transfer Protocol Secure): is the secure version of HTTP. It claims to send data securely over the internet. For example, passwords, credit card information, and so on.
FTP: When we wish to transmit a file from one computer to another, we utilise FTP (File Transfer Protocol).
SMTP: The Simple Mail Transfer Protocol (SMTP) is a protocol for sending and receiving emails over the internet.
Host: A Host is anything that is a part of the network that wishes to communicate.
Server: A server is a unique kind of computer. When accepting data from customers, it also acts as a Host. A server is a device from which a host receives data.
Good luck and happy learning!