Digital Signature: A Secure Way to Validate Digital Documents
Back to home
- Introduction
- What is a Digital Signature?
- What is a digital identity?
- Related Terms to Digital Signature
- How Does a Digital Signature Work?
- How to Create a Digital Signature?
- Importance of Digital Signature
- Benefits of Using Digital Signatures
- Industries That Use Digital Signatures
- What’s the difference between a digital signature and an electronic signature?
- What is a digital certificate? what it contains ?
- Differentiate between the Digital Certificate and Digital Signature/a>
- What is Public Key Infrastructure (PKI)?
- What is a Certificate Authority (CA)?
- Are Digital Signatures Legal and Secure?
- Future of Digital Signatures
- Conclusion
𝑻𝒂𝒃𝒍𝒆 𝒐𝒇 𝑪𝒐𝒏𝒕𝒆𝒏𝒕

 Logicmojo - Updated July 24, 2022
Logicmojo - Updated July 24, 2022
Introduction
In today's fast changing digital world, where the vast majority of transactions and conversations take place over the internet, the need to ensure the authenticity and integrity of digital documents has become critical. In such a scenario, the digital signature emerges as a potent cryptographic instrument, providing a safe and reliable technique of verifying the authenticity of digital files and messages. The relevance of digital signatures cannot be emphasized, given the increasing dependence on digital data and the potential threats posed by unauthorized modifications or frauds.
Digital signatures have several uses in a variety of sectors. The introduction of digital signatures has altered several industries, from the banking sector, where secure online transactions and identity verification are critical, to the healthcare business, where medical professionals rely on digital signatures to validate electronic medical data.
As businesses and organizations continue to move to digital operations, the importance of digital signatures in protecting information and building confidence in the digital sphere is expected to grow.
This article focuses into the notion of digital signatures, as well as its relevance and uses in numerous sectors.
What is a Digital Signature?
A digital signature is a sophisticated and robust mathematical technique utilized to ensure the trustworthiness of a digital document, message, or software in the vast and dynamic digital landscape. Think of it as a virtual equivalent of a handwritten signature that provides an added layer of security and validation to digital transactions and communications.
At its core, the digital signature is founded on the principles of public-key cryptography. The process begins with the individual or entity who intends to sign the document, often referred to as the signer. The signer possesses a pair of cryptographic keys: a private key and a corresponding public key. These keys are intricately related but serve distinct purposes.
Digital signatures can be used to verify the origin, identity, and status of electronic documents, transactions, or digital messages. They can also be used by signers to acknowledge informed consent. Digital signatures are legally binding in many nations, including the United States, United Kingdom, Canada, and Australia, in the same way that traditional handwritten document signatures are.
A digital signature method is usually made up of three algorithms:
Key Generation Algorithms: A digital signature is an electronic signature that confirms that a communication was transmitted by a certain sender. Authenticity and integrity should be ensured while conducting digital transactions; otherwise, the data can be manipulated or someone might pretend to be the sender and expect a response.
Signing Algorithms: Signing algorithms, such as email programs, generate a one-way hash of the electronic data to be signed in order to form a digital signature. The hash value is subsequently encrypted by the signing algorithm using the private key (signature key). The digital signature consists of this encrypted hash, as well as other information such as the hashing technique. This digital signature is attached to the data and transmitted to the verifier. Because a hash function turns any arbitrary input into a much shorter fixed-length result, encrypting the hash rather than the full message or document makes sense. This saves time because instead of signing a big message, a shorter hash value is now required to be signed, and hashing is significantly quicker than signing.
Signature Verification Algorithms: Along with the data, the Verifier obtains the Digital Signature. It then applies the Verification algorithm to the digital signature and the public key (verification key) to create a value. It also uses the same hash function to produce a hash value from the supplied data. The hash value and the verification algorithm output are then compared. If they are both equivalent, the digital signature is genuine; otherwise, it is invalid.
What is a digital identity?
A digital identity, also known as a digital ID, is akin to an electronic passport in the digital realm. It serves as a virtual representation of an individual's or entity's identity and plays a crucial role in establishing trust and authenticity in online interactions. Just as a physical passport validates one's identity when traveling internationally, a digital ID provides strong evidence that an individual is indeed who they claim to be in the digital space.
The process of obtaining a digital ID involves a thorough verification of the individual's identity by a trusted third party, such as a bank, government agency, or a certified identity provider. This verification process ensures that the digital identity is linked to the correct person or entity, mitigating the risk of impersonation and fraudulent activities.
When using a digital ID to authenticate one's identity during the process of e-signing a document, it serves as a powerful affirmation that the signer is legally and legitimately associated with the e-signature applied to the specific document. By leveraging a digital ID, individuals can confidently assert that they have agreed to the terms outlined in the document and have authorized the use of their e-signature in a legally binding manner.
The connection between a digital identity and a digital signature is vital in ensuring the integrity and security of the e-signing process. When a signer's digital identity is verified and linked to their digital signature, it establishes a strong chain of trust and accountability. The digital signature, generated using the signer's private key, is uniquely tied to their verified digital identity. Any attempt to alter the document or use a different signature would be detected as invalid, as it would not match the verified digital identity associated with the signer.
Related Terms to Digital Signature
• Encryption:
Encryption is a process of converting plain text or data into a coded form, known as ciphertext, using an algorithm and a key. It ensures data confidentiality and prevents unauthorized access to sensitive information.
• Decryption:
Decryption is the reverse process of encryption. It involves converting ciphertext back into its original plaintext using the appropriate decryption algorithm and key.
Types of Encryption:
There are two main types of encryption: Symmetric Encryption and Asymmetric Encryption.
1. Symmetric Encryption:
Symmetric encryption uses a single secret key for both encryption and decryption. It is efficient for bulk data encryption but requires a secure channel to share the key.
2. Asymmetric Encryption:
Public-key cryptography is another name for asymmetric cryptography. Asymmetric encryption involves a pair of keys: a public key and a private key. The public key is used for encryption, while the private key is used for decryption. It provides a secure way to exchange information without the need for a shared secret key.
• Public Key: A public key is part of an asymmetric key pair and is freely shared with others to encrypt data intended for the owner of the corresponding private key.
• Private Key: The private key is the counterpart of the public key and must be kept confidential. It is used to decrypt data encrypted with the corresponding public key.
• Authentication: Authentication is the process of verifying the identity of a user, device, or system to ensure that the claimed identity is genuine.
• Non-Repudiation: Non-repudiation ensures that the sender of a message or document cannot deny its authenticity or origin, providing proof of the sender's involvement.
• Integrity: Integrity ensures that data remains unaltered and complete during transmission and storage, protecting it from unauthorized modifications.
• Message Digest: A message digest, also known as a hash value, is a fixed-size output generated from an input data using a cryptographic hash function. It acts as a unique digital fingerprint of the original data.
Relation to Digital Signature:
Digital signatures are closely related to the concepts mentioned above. When creating a digital signature:
- Encryption: The digital signature process involves encryption, where the signer uses their private key to encrypt the hash value of the document, resulting in the digital signature.
- Decryption: The recipient uses the signer's public key to decrypt the digital signature, revealing the original hash value for verification.
- Asymmetric Encryption: Digital signatures use asymmetric encryption to provide authentication and non-repudiation. The signer uses their private key to sign the document, while anyone with access to the public key can verify the signature.
- Public Key and Private Key: The public key is used to verify the digital signature, while the private key is used to create the signature.
- Authentication and Non-Repudiation: Digital signatures ensure the authenticity of the signer and the document, providing authentication and non-repudiation.
- Integrity: The digital signature ensures the integrity of the document by verifying that it has not been altered or tampered with since it was signed.
- Message Digest: The digital signature relies on the message digest or hash value of the document to create and verify the signature, ensuring that the content remains unchanged.
How Does a Digital Signature Work?
Each signer's own digital signature is distinct, much like its handwritten equivalent. DocuSign and other digital signature solution providers adhere to a standard known as Public Key Infrastructure, or PKI. PKI requires the provider to produce two lengthy integers known as keys using a mathematical process. One key is public, while the other is secret.
When a signer electronically signs a document, the signature is made using the signer's private key, which the signer always keeps securely. The mathematical algorithm functions as a cipher, generating data that matches the signed document, known as a hash, and encrypting that data. The digital signature is created as a result of the encrypted data. The signature is also accompanied with the moment the paper was signed. If the document is changed after signing, the digital signature is rendered invalid.
As an instance, Daksh uses her private key to sign a contract to sell a timeshare. The document is given to the buyer. The document's purchaser also obtains a duplicate of Daksh's public key. The signature isn't Daksh's or has been altered since it was signed if the public key cannot decrypt it using the cipher from which the keys were generated. The signature is then deemed to be fake.
PKI demands that the keys be generated, handled, and maintained securely to guarantee the integrity of the signature; this frequently necessitates the assistance of a trustworthy Certificate Authority (CA). DocuSign and other digital signature service providers adhere to PKI standards for secure digital signing.
How to Create a Digital Signature?
A one-way hash of the electronic data to be signed is provided by signing software, such as an email program, to establish a digital signature.
A digital signature must be created in a methodical manner using a number of processes to guarantee its security and integrity. Here is a thorough breakdown of each phase, along with an example flowchart, to help you understand the procedure:
Step 1: Create the Document
• The first step in creating a digital signature is to prepare the document that needs to be signed. This document can be any digital file, such as a text document, PDF, or an image. The signer, who intends to apply the digital signature, ensures that the content of the document accurately reflects the information or message they wish to endorse.
Step 2: Hash the Document
• Once the document is ready, the next step is to generate a fixed-size hash value based on the content of the document. A cryptographic hash function is employed to calculate this hash value. The hash function takes the entire content of the document as input and produces a unique, fixed-length string of characters, known as the hash.
• The purpose of hashing the document is twofold: First, it condenses the entire document into a concise and fixed-size representation. Second, it acts as a digital fingerprint of the document's content. Even a minor change in the document's content would result in a completely different hash value.
Step 3: Sign the Hash
• In this step, the signer utilizes their private key to encrypt the generated hash value. This encryption process is akin to locking the hash value with the signer's private key, creating what is known as the digital signature. The private key serves as the signer's unique and secret identifier, ensuring that only the signer possesses the means to generate the signature.
• The digital signature, which is essentially the encrypted hash value, is now associated with the specific document. It verifies the authenticity of the signer and ensures that the document remains unchanged since it was signed.
Step 4: Attach the Digital Signature
• With the digital signature created, the final step is to attach it to the original document. The digital signature is incorporated into the document in such a way that it remains linked to the content, and any subsequent changes to the document would be detectable.
• The document, along with the attached digital signature, can now be securely transmitted or shared with recipients. The recipients can use the signer's public key to verify the digital signature and ensure the document's authenticity and integrity.
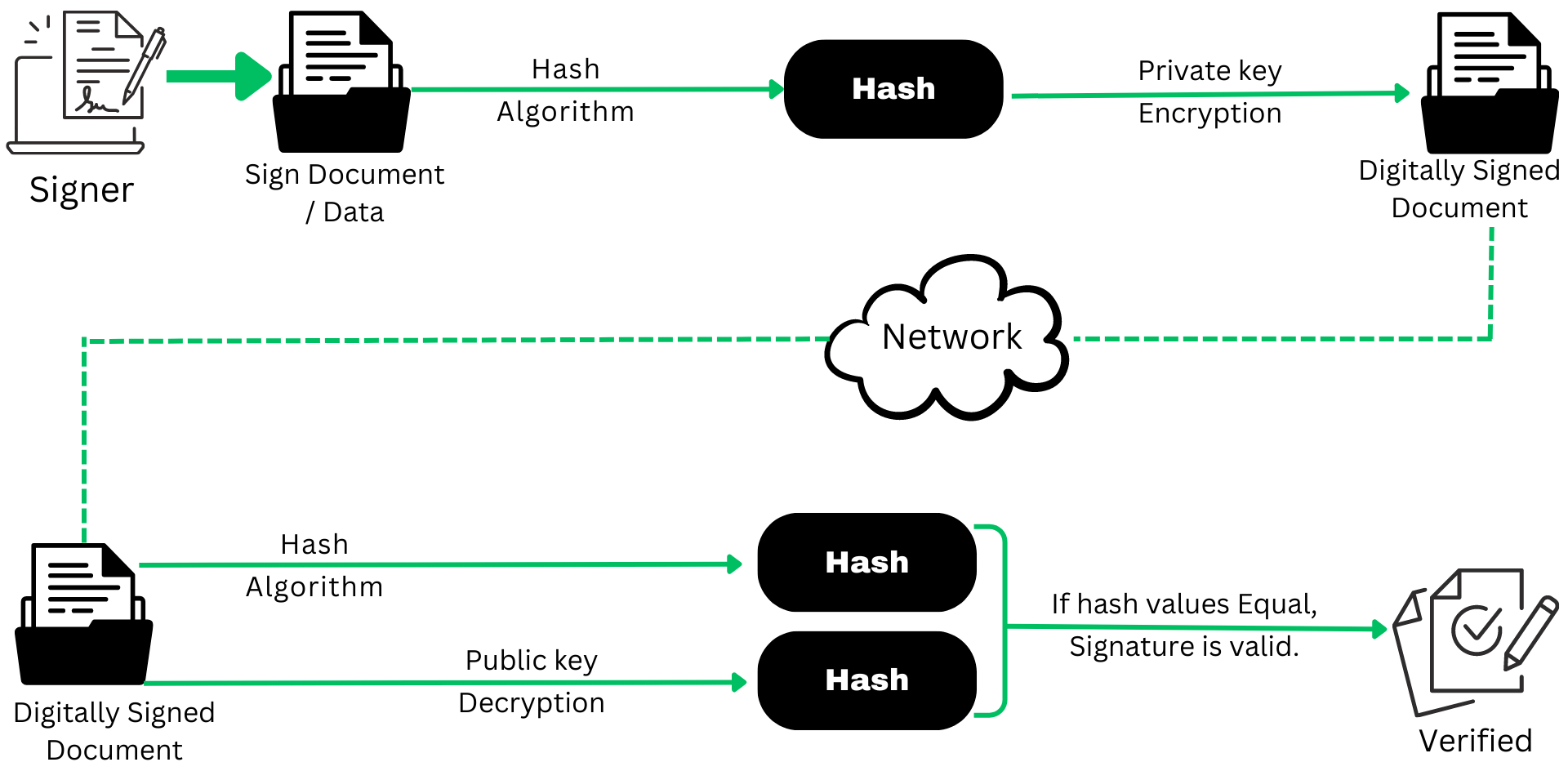
Any message, encrypted or not, may utilize a digital signature so that the recipient can be certain of the sender's identity and that the message was sent in tact. Because a digital signature is specific to both the document and the signer and links them together, it is challenging for the signer to claim not to have signed something. This characteristic is known as nonrepudiation.
The digital certificate is the electronic file bearing the issuing CA's digital signature. It is what links a public key to an identity and enables users to confirm that a given person or business is the owner of a certain public key. The majority of contemporary email clients allow the use of digital certificates and signatures, making it simple to check digitally signed receiving messages and sign any emails that are sent out.
Importance of Digital Signature
Public key cryptography-based digital signatures are regarded as one of the most crucial and practical tools for achieving information security out of all the cryptographic primitives. The digital signature also offers data integrity and message authentication in addition to non-repudiation of the message. Let's take a quick look at how the digital signature does this.
Message authentication: When a sender's public key is used to authenticate a digital signature, the verifier is confident that the signature has only been created by that sender and no one else.
Data Integrity: The digital signature verification at the receiving end is ineffective if an attacker gains access to the data and alters it. The output of the verification procedure will not match the hash of the updated data. Therefore, presuming that data integrity has been compromised, the receiver can safely reject the message.
Non-repudiation: The signer can only produce a unique signature on the given data because it is presumed that only he or she knows the signature key. As a result, if a dispute ever occurs, the receiver can show data and the digital signature to a third party as proof.
We can develop a cryptosystem that can provide the four fundamental components of security, namely privacy, authentication, integrity, and public key, by incorporating public-key encryption into digital signature schemes.
Benefits of Using Digital Signatures
Enhanced Security: Digital signatures use encryption technology, making it nearly impossible for unauthorized parties to forge or alter the signature. Asymmetric cryptography, PINs, checksums, and cyclic redundancy checks (CRCs), as well as CA and trust service provider (TSP) validation, are security features.
Time and Cost Savings: Asymmetric cryptography, PINs, checksums, and cyclic redundancy checks (CRCs), as well as CA and trust service provider (TSP) validation, are security features. Digital signatures make it easier for businesses to obtain and sign documents rapidly by streamlining the laborious processes involved in traditional document signing, storage, and exchange. By becoming paperless, businesses can save money on the materials, labor, staff, and office space traditionally required to store, handle, and transfer papers.
Eco-Friendly: By reducing the need for paper documents, digital signatures contribute to environmental conservation efforts.
Global Acceptance: Digital signatures are legally recognized in many countries around the world, making them a widely accepted method of authentication. As digital signatures become the norm globally, more nations are recognizing their legal significance.
Traceability: With the use of digital signatures, firms can maintain internal records more easily. There are less chances for a manual signer or record keeper to make a mistake or lose something when everything is recorded and stored digitally.
Legal documents and contracts: Legal contracts are signed digitally. They are therefore perfect for any legal document that calls for a signature that is verified as valid by one or more parties and ensures that the record hasn't been changed.
Financial Documents: To ensure that payment requests come from the legitimate vendor and not from a dishonest third party attempting to dupe the buyer into sending funds to a phony account, finance departments digitally sign invoices.
Industries That Use Digital Signatures
Digital signatures have become an indispensable tool across various industries, revolutionizing the way businesses conduct transactions, secure sensitive information, and ensure data integrity. Let's explore how digital signatures are applied in different sectors:
Financial Sector:
In the fast-paced world of banking and finance, digital signatures play a pivotal role in facilitating secure online transactions and authenticating client verifications. By employing digital signatures, financial institutions can enhance the efficiency of processes such as fund transfers, loan approvals, and account openings, while also mitigating the risks associated with fraudulent activities.
Healthcare:
In the healthcare industry, where the accuracy and privacy of medical records are of utmost importance, digital signatures offer a reliable means for medical professionals to sign and authenticate electronic medical records (EMRs). By adopting digital signatures, healthcare providers can ensure the integrity of patient data, expedite the sharing of medical information, and streamline administrative tasks, ultimately leading to improved patient care and confidentiality.
Government:
Government agencies handle a vast array of sensitive documents and communications, and digital signatures provide a secure and efficient way to ensure authenticity and confidentiality. From secure communication between government entities to document authentication for legal purposes, digital signatures play a crucial role in enhancing data security and reducing paperwork in government processes.
Real Estate:
The real estate industry has witnessed a significant transformation with the adoption of digital signatures. Gone are the days of cumbersome paperwork and time-consuming manual signings. Digital signatures streamline the process of signing contracts and legal documents, enabling buyers, sellers, and agents to execute agreements quickly and securely, regardless of their physical locations.
Manufacturing:
Digital signatures have found applications in the manufacturing sector, where they expedite various processes throughout the product lifecycle. From product design and quality assurance to manufacturing enhancements, marketing, and sales, digital signatures enhance efficiency and streamline workflows. Manufacturers can validate product specifications, approvals, and agreements digitally, accelerating decision-making and reducing the reliance on physical paperwork.
Cryptocurrencies:
Cryptocurrencies, such as Bitcoin, rely heavily on digital signatures to authenticate and secure transactions on the blockchain. Digital signatures are used to generate and verify digital signatures, which ensure the integrity and authenticity of cryptocurrency transactions. Users can demonstrate ownership of currency or their involvement in a transaction through digital signatures, thereby establishing trust in the decentralized cryptocurrency ecosystem.
What’s the difference between a digital signature and an electronic signature?
The concept of a "e-signature," often known as an electronic signature, is legally defined. An electronic signature known as a "digital signature" calls for a more precise level of identity assurance using digital certificates.
Many different types of electronic signatures fall under the umbrella term "e-signatures," or electronic signatures. Digital signatures, a particular technological application of electronic signatures, are included in this category. You can sign papers and verify the signer using digital signatures and other e-signature programs. However, compared to other forms of e-signatures, digital signatures have different uses, technical implementations, geographic applications, and legal and cultural acceptance.
The use of digital signature technology for e-signatures differs significantly between nations, in particular between those that follow tiered eSignature models that prefer locally defined standards based on digital signature technology, such as many in the European Union, South America, and Asia, and those that follow open, technology-neutral e-signature laws, such as the United States, United Kingdom, Canada, and Australia. The Advanced Electronic Signature (AES) and Qualified Electronic Signature (QES) are the two types of digital signatures recognized in the European Union under the eIDAS law. Specific standards based on digital signature technology are also supported by various sectors.
| Digital Signature | Electronic Signature (e-sign) |
|---|---|
| It uses a cryptographic procedure and an algorithm to check a series of data in order to determine the author of a signature and the legitimacy of a document. | It utilizes electronic symbols, sounds, or operations. tied to or linked to a contract or record to confirm a signature's authorship. |
| A certificate authority must issue the certificate. | Any signature that has been applied electronically |
| It is one kind of electronic signature. | E-sign is a more general phrase whose definition includes digital signature |
| It provides cryptographic evidence of a document's integrity and authenticity as well as the signature of the signer. | It confirms a signer's intention to sign a document, but it doesn't always show the signer's identity or the reliability of the document. |
The following three requirements must be met by e-signature systems in order to be valid:
1. a means of confirming the signer's legitimacy.
2. a means of determining if the party signing the document had the intent to confirm it.
3. a means of confirming the e-signature's connection to the signed document.
What is a digital certificate? what it contains ?
A digital certificate is a crucial component of the Public Key Infrastructure (PKI) that serves as an electronic document issued by a trusted entity known as a Certificate Authority (CA). It plays a fundamental role in ensuring the security and authenticity of digital communications and transactions. The digital certificate contains essential information, including a public key and details about the identity associated with that key, such as the name of an organization or an individual.
The digital certificate acts as a digital identity card, confirming the ownership of the public key by the specified organization or individual. It is digitally signed by the Certificate Authority, establishing trust and providing assurance that the information within the certificate is accurate and valid. By verifying the certificate's authenticity and the CA's digital signature, users can trust that the public key indeed belongs to the claimed entity, thereby establishing a secure and reliable communication channel.
Digital certificates have a limited validity period and must be reissued or renewed periodically by the trusted Certificate Authorities. By adhering to the PKI framework and utilizing digital certificates issued by reputable CAs, organizations and individuals can establish secure and trustworthy digital interactions, safeguarding sensitive information and enabling a wide range of secure online activities, including secure communication, digital signing, and encryption.
Differentiate between the Digital Certificate and Digital Signature
Here's a table highlighting the main differences between digital certificates and digital signatures:
| Aspect | Digital Certificate | Digital Signature |
|---|---|---|
| Purpose | Electronic document issued by Certificate Authorities (CAs) to verify the identity of an entity and associate it with a public key. | Cryptographic technique used to sign and authenticate digital documents or messages. |
| Contents | Contains the public key, entity's identity (e.g., organization name), expiration date, and CA's digital signature. | Created using the signer's private key and includes the signed data and a hash of the data. |
| Issued by | Issued by a trusted Certificate Authority (CA) or a self-signed certificate (less secure). | Created and issued by the signer themselves. |
| Verification | Used to verify the authenticity and identity of the entity associated with the public key. | Used to verify the integrity and authenticity of a digitally signed document or message. |
| Usage | Used to establish secure communication channels, enable digital signatures, and validate SSL/TLS connections. | Employed to sign documents, emails, or messages to prove the authenticity and integrity of the content. |
| Trust and Security | Relies on the trustworthiness of the issuing CA; the security of the private key is crucial. | Depends on the security of the signer's private key; tampering with the signed data invalidates the signature. |
| Relationship to Data | Provides assurance that the public key belongs to the specified entity, but not linked to specific data. | Directly linked to the specific data it signs; changes to the data invalidate the signature. |
| Duration of Validity | Has a limited validity period and must be periodically renewed or reissued. | Valid as long as the private key remains secure and the signature is not invalidated by changes to the data. |
| Application | Used in secure online transactions, digital signing, encryption, and secure communication. | Utilized to ensure data integrity, prove the authenticity of documents, and prevent tampering. |
What is Public Key Infrastructure (PKI)?
The Public Key Infrastructure (PKI) is a collection of standards that allows for the generation of digital signatures, among other things. Through PKI, a private key and a public key are included in every digital signature transaction. The private key, as its name suggests, is only used by the signer to digitally certify documents. Those that need to verify an electronic signature are able to do so by using the public key, which is made available to the public. The Certificate Authority (CA), a digital certificate, end-user enrolment software, and tools for managing, renewing, and revoking keys and certificates are some of the extra criteria enforced by PKI.
The Pretty Good Privacy (PGP) encryption program and the PKI standard are both used in digital signatures to minimize any potential security risks associated with transmitting public keys. They authenticate the sender's identity and confirm that the sender's public key indeed belonged to that person.
Public key infrastructure (PKI) is a framework for services that create, manage, distribute, and track public key certificates. Symmetric key and public key cryptography are used in PGP, a variant of the PKI standard, although it differs in how it links public keys to user identities. PKI uses a web of trust, whereas PGP uses a CA to validate and associate a user identity with a digital certificate. PGP users decide which identities to verify and who they trust. PKI users obey trustworthy CAs.
What is a Certificate Authority (CA)?
Public and private keys are necessary for digital signatures. These keys must be secured in order to maintain security and prevent theft or malicious use. You require confirmation that the documents and the keys were generated securely and that they are utilizing legitimate keys before you send or sign a document. Organizations that have been generally recognized as trustworthy for maintaining key security and that are able to offer the appropriate digital certificates are known as certificate authorities (CAs), a subset of trust service providers. The CA must be used by both the transmitting entity and the recipient who sign the document.
A CA is DocuSign. This means that utilizing DocuSign as the Certificate Authority will always allow you to deliver a document with a digital signature. As an alternative, you can access the robust functionality of DocuSign cloud services for transaction management by using a third-party Certificate Authority. The DocuSign platform also supports additional well-known CAs, which are used by some organizations or regions. These include SAFE-BioPharma, an identity credential that life science businesses may choose to adopt, and OpenTrust, which is popular in nations of the European Union.
Are Digital Signatures Legal and Secure?
1. Legally Binding and Recognized:
Digital signatures are legally recognized and accepted as a valid form of authentication in many countries and across various industries. Governments and regulatory bodies in numerous jurisdictions have enacted laws and regulations to provide legal validity to digital signatures. For example, the Electronic Signatures in Global and National Commerce Act (ESIGN Act) in the United States and the eIDAS Regulation in the European Union establish the legal framework for digital signatures and their equivalence to traditional handwritten signatures.
2. High Level of Security and Tamper Resistance:
Digital signatures provide a high level of security, offering robust protection against tampering and unauthorized alterations of digitally signed documents. The core security lies in the unique cryptographic process employed during signature creation. When a document is digitally signed, it is combined with a hash value generated from its content. This hash value acts as a unique fingerprint of the document.
Additionally, digital signatures are often complemented by Public Key Infrastructure (PKI), which involves the use of trusted Certificate Authorities (CAs) to issue digital certificates. These certificates further enhance the security and trustworthiness of digital signatures by confirming the identity of the signer and ensuring that the public key used for verification indeed belongs to the claimed entity.
Future of Digital Signatures
Increased Adoption and Integration:
As the world continues to embrace digital transformation, the adoption of digital signatures is expected to surge across various industries and sectors. Businesses and organizations are recognizing the efficiency, cost-effectiveness, and environmental benefits of transitioning from paper-based processes to digital alternatives. With digital signatures offering legally binding and secure authentication, they are poised to become an integral part of everyday transactions, agreements, and communications.
Advancements in Security and Blockchain Technology:
As technology evolves, so will the security measures surrounding digital signatures. Advancements in cryptographic algorithms and key management will continue to fortify the security of digital signatures, making them even more robust against potential threats and attacks. Secure key generation, management, and storage practices will be further refined to prevent unauthorized access and enhance overall data protection.
Conclusion
Digital signatures have revolutionized the way we authenticate and validate digital documents, bringing trust and security to the online world. By harnessing the power of cryptography, digital signatures provide an efficient, secure, and legally recognized method of ensuring document integrity. Embracing this technology not only streamlines various processes but also safeguards against fraudulent activities.
Good Luck & Happy Learning!!
Frequently Asked Questions (FAQs)
To create a digital signature, follow these main points:
1. Obtain a Digital ID: Acquire a digital identity (digital ID) from a trusted third party, such as a government agency or a certified identity provider.
2. Generate Key Pair: Create a cryptographic key pair consisting of a private key (kept confidential) and a corresponding public key.
3. Hash the Data: Use a cryptographic hash function to generate a fixed-size hash value of the data you want to sign.
4. Sign the Hash: Encrypt the hash value using your private key to create the digital signature.
5. Attach Signature: Attach the digital signature to the original data, creating the digitally signed document.
By following these steps, you can create a secure and verifiable digital signature for your documents.
A digital signature is a cryptographic technique used to sign and authenticate digital documents or messages. When a signer digitally signs a document, the following process takes place:
- Generate Cryptographic Hash: A cryptographic hash is generated for the document, creating a unique fixed-size representation of its content.
- Encrypt with Private Key: The cryptographic hash is encrypted using the sender's private key, which is securely stored in a Hardware Security Module (HSM) box.
- Append to Document: The encrypted hash, known as the digital signature, is appended to the document, effectively linking it to the signed content.
- Send to Recipients: The digitally signed document is sent to the recipients along with the sender's public key, allowing them to verify the signature's authenticity.
This process ensures that the digital signature is unique to the document and the signer. By encrypting the hash with the sender's private key, the signature becomes tamper-resistant. Recipients can use the sender's public key to decrypt and verify the signature, confirming the document's authenticity and integrity.
Yes, digital signatures can be free to use for certain electronic signature services. For example, DocuSign offers a free electronic signature tool that allows users to electronically sign documents on various devices. The main points to note about free digital signatures are:
- Electronic Signature Tool: DocuSign provides a free electronic signature tool that enables users to sign documents electronically.
- Sign Documents Anywhere: Users can add an electronic signature to documents using a computer, tablet, or mobile phone.
- Wide Range of Uses: With the free tool, users can sign forms, contracts, and agreements in minutes.
- Simple Process: To sign a document with an electronic signature, users only need to upload the document and follow the guided steps.
Overall, the availability of free electronic signature tools like DocuSign makes it convenient and accessible for individuals and businesses to sign and receive signed documents electronically without incurring additional costs.
Yes, thanks to technological advancements, a handwritten signature can now be created digitally. This process allows individuals to retain their personal signature style while embracing the benefits of electronic signatures. The main points to consider are:
1. Handwritten Signature Replication: With online tools and applications, it is now possible to replicate your handwritten signature digitally. These tools use various techniques, such as signature pads, touchscreens, or stylus pens, to capture the unique characteristics of your handwritten signature.
2. Personal Signature Style: The beauty of digital handwritten signatures lies in the ability to preserve your individual signature style. The process captures the nuances and details of your handwritten signature, ensuring that the digital version closely resembles your pen-and-paper signature.
3. Benefits of Electronic Signatures: By digitizing your handwritten signature, you can leverage the advantages of electronic signatures. Electronic signatures offer convenience, speed, and security in signing digital documents, making them ideal for various applications, including contracts, agreements, and forms.
4. Enhanced Efficiency: The digital nature of handwritten signatures streamlines document signing processes. Users can sign documents online from anywhere, eliminating the need for physical presence or printing and scanning documents.
5. Legal Validity: When implemented correctly, digitally created handwritten signatures are legally binding in many jurisdictions. Organizations and businesses recognize these signatures as valid and trustworthy, ensuring their acceptance in official transactions.
6. Authentication Measures: To ensure security and prevent forgery, digital handwritten signature solutions often employ authentication measures, such as biometric verification or cryptographic algorithms.
The primary use of a digital signature is to confirm the integrity and authenticity of a digital message or document. This cryptographic technique plays a crucial role in ensuring data security and verifying the identity of the sender or organization. The main points to consider are:
1. Integrity Confirmation: A digital signature provides assurance that the contents of a digital message or document have not been tampered with or altered since the time of signing. By creating a unique hash value of the data and encrypting it with the signer's private key, any modification to the signed data would invalidate the signature, thus safeguarding against unauthorized changes.
2. Origin Authentication: The digital signature authenticates the origin of the message or document. It serves as a digital fingerprint uniquely linked to the signer, verifying that the information indeed originated from the claimed sender. The recipient can verify the digital signature using the signer's public key, ensuring that the data is from the intended source.
3. Non-Repudiation: Digital signatures offer non-repudiation, meaning the signer cannot deny their involvement in the signing process. Since the digital signature is uniquely tied to the signer's private key, the signer cannot refute their role in signing the document, ensuring accountability and trustworthiness in digital transactions.
4. Legal Validity: Digital signatures are legally recognized and accepted in many countries as a valid form of authentication. They hold the same legal standing as handwritten signatures, making them suitable for a wide range of applications, including contracts, agreements, financial transactions, and official documents.
5. Secure Communication: By confirming the integrity and authenticity of digital messages, digital signatures provide a secure means of communication. Organizations can use digital signatures to ensure that sensitive information remains unaltered and comes from verified sources, reducing the risk of data breaches and unauthorized access.
Adding a digital signature to a PDF document is a straightforward process that can be accomplished using Adobe Acrobat Reader. Here are the main points to follow:
- Open PDF in Adobe Acrobat Reader: Begin by opening the PDF file in Adobe Acrobat Reader. If you don't have it installed, you can download it for free from Adobe's website.
- Access Fill & Sign: In the Tools panel located on the right-hand side of the interface, click on "Fill & Sign." This tool allows you to add your signature to the PDF.
- Choose Signature Option: Click on "Sign" from the options provided, and then select "Add Signature." A popup will appear, offering different ways to create your signature.
- Signature Creation: You have three options to create your signature:
- Type: Type your name and choose from a range of fonts to create a signature-like appearance.
- Draw: Use your mouse or touchpad to draw your signature directly on the screen.
- Image: Upload an image of your hand-written signature for use in the PDF.
- Apply Signature: Once you have created or selected your signature, click "Apply" to add it to the PDF.
- Position Signature: After applying the signature, you can drag, resize, and position it inside the PDF document to the desired location.
- Save Document: Finally, save the PDF document with the added digital signature to preserve the changes.
By following these steps, you can easily create and add a digital signature to your PDF files using Adobe Acrobat Reader, making them secure and legally binding for various professional and personal purposes.
To convert your handwritten signature into a digital signature, follow these main steps:
- Handwritten Signature: Start by writing your signature clearly on a piece of paper. Use black ink on white paper to achieve maximum contrast, ensuring that your signature shows up clearly and legibly.
- Scanning the Document: Once you have your paper document with the handwritten signature, use a scanner to digitize it. Scan the document at the highest possible resolution to capture all the details and intricacies of your signature.
- Save as Image File: After scanning, save the digitized signature as an image file. The recommended formats are JPG or PNG, as they maintain the quality and clarity of the signature.
By following these steps, you will successfully convert your handwritten signature into a digital signature that can be easily used for electronic signing of documents. The scanned image file preserves the authenticity and uniqueness of your handwritten signature, allowing you to add it to digital documents and applications.
To add or change a digital signature on your phone, follow these main points:
- Access Settings: Start by scrolling to the bottom of your phone screen and tapping on "Settings."
- Select Google Account: In the Settings menu, choose the Google Account where you want to add or change the signature for your emails.
- Tap Mobile Signature: Look for the option "Mobile Signature" and tap on it. This setting allows you to customize the text that will appear as your digital signature in mobile emails.
- Enter Your Signature: In the Mobile Signature section, enter the text that you want to use as your digital signature for outgoing emails. You can use your name, title, contact information, or any personalized message you prefer.
By following these steps, you can easily create or modify your digital signature for mobile emails on your phone. Your digital signature will be automatically added to the bottom of the emails you send from that particular Google Account, providing a professional touch to your mobile correspondence.
When verifying a digital signature, the following main points come into play:
- Decryption with Public Key: To verify a digital signature, the recipient or verifier uses the signer's public key to decrypt the signature. The public key is freely available and can be shared openly.
- Original Hash Value: The decryption process yields a hash value, which is a unique representation of the data that was signed. The hash value is created by applying a cryptographic hash function to the original data.
- Matching Hash Values: The verifier then compares the decrypted hash value with a newly calculated hash value based on the received data. If the two hash values match, it indicates that the signature has been verified.
Through this process, the recipient can ensure the integrity and authenticity of the digital message or document. If the signature is valid and unchanged, the hash values will match, confirming that the data has not been tampered with since it was signed. On the other hand, if the hash values do not match, it signifies that the data has been altered, and the signature is considered invalid.
By employing public-key cryptography and the comparison of hash values, the verification of a digital signature provides a robust mechanism for confirming the legitimacy of digital documents and messages, bolstering trust and security in electronic transactions.
To add a digital signature in Word, follow these main points:
- Place Cursor: Click on the area in the Word document where you want to insert your signature. This can be at the end of the document or wherever the signature is required.
- Insert Signature Line: Under the "Insert" tab in Word, locate and select the "Signature Line" option. This will prompt a pop-up window to appear.
- Input Signature Details: In the pop-up window, enter your signature details, such as your name, title, and any other relevant information. You can also add instructions or remarks for the signer, if necessary.
- Finalize Signature Line: After entering the required information, click "OK" to finalize the signature line in the document.
- Write and Capture Signature: Write your signature on a piece of paper and then take a photo of it using a digital camera or smartphone.
- Save Signature Photo: Save the captured photo of your signature to your computer or any desired location for later use.
With these steps, you have successfully created a digital signature in Word. The signature line provides a space for you or others to insert your signature image, ensuring a professional and personal touch to your digitally signed documents.





